Windows 10 Insider: integrated SSH server
As far as I can remember, Microsoft Windows only had a Telnet server integrated, if we don’t count recent PowerShell Remoting (using Windows Remote Management, or WinRM). Still, it wasn’t SSH. Since 14352, people were finding traces, of what proved to be an integrated Microsoft SSH Server for Windows. Because Microsoft is also contributing to OpenSSH for Windows project, and that it’s getting to a fairly usable stage, I found the inclusion of the service quite interesting.
SSH server on Windows? Are you insane?
No.
First, I’ve been using SSH server on my Windows machines for quite some time now. It has always been a Cygwin-based solution, though. This SSH and SFTP server allowed me to access my files remotely and do some basic work with them, as well as launch some command-line apps. (I wasn’t fan of launching Windows apps through CLI, but it did prove useful at times.
Last year, a bomb was dropped by a PowerShell team in Microsoft, where they announced that they are going to adopt OpenSSH and modify it so that it can run on Windows and use Windows crypto. And, of course, they wanted to push the changes back upstream. This was a major announcement because, up to that point, Microsoft management always refused to allow SSH work, for one reason or another.
As the year went, PowerShell team posted another update with a nice large slice of completed work and first public release. Since then, there have been more releases and precompiled binaries for all releases are available at their Github releases page. Both key-based and password-based (interactive) auth is supported and the terminal works somehow. SFTP also works.
Twist: Microsoft’s own SSH server
But, a Microsoft’s own SSH server has made a quiet appearance in 14352, where two new services popped up in services.msc:
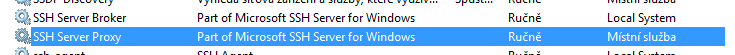
Surprise? Depends on who you ask. It was a surprise for me, for reasons that I’ve outlined above, but splipstream/RoL on Twitter actually pointed out that SSH/SFTP server is present in both Windows 10 Mobile (in developer mode) and Windows 10 IoT Core for quite some time now.
What’s more: There’s a Microsoft guide for using SSH in Windows IoT and unofficial guide for accessing SFTP on Windows 10 Mobile on XDA, because the SSH server was apparently used to activate Android subsystem on Windows, among other things.
But the SSH server in full Windows 10 is a bit different. Mainly because you can play with the settings.
What can it do?
It can provide you with a cmd.exe. But that’s not all, folks!
First: why two services?
- The broker essentially serves as the SSH server and proxy provides this server to the world by binding it to a port 22.
- So maybe it can be used locally in another fashion.
Second: how do I log in?
- With your user name and password
- Then, you cannot actually run anything, since it gets shot down right after launch. God MS knows why.
- Because of that, it has (more or less) capabilities of the good old restore command prompt in Windows XP installer.
- With
DevToolsUser- This is a special user that logs in as the last logged in user
- I think that some dev tools from MS use this account internally, but so far I have to see a tool that uses it. I would guess it’s used for remote debugging and/or deployment
- A PIN can be added in the registry, which allows you to log in with that PIN
- This account gets the rights of the currently logged in user, and allows you to run everything under that user. (UAC still applies, and you can even run desktop apps, as it will, literally, log you in under the last logged-in account - not the one that was last used!)
You can actually take a look for yourself: the registry key is HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Ssh. When you then use Process Monitor from Sysinternals, you can exactly see which keys the services access.
Third: how do I transfer files?
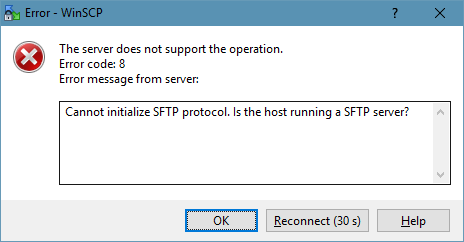
- You don’t. Actually, you do, through SFTP. Midnight Commander was able to connect. For some reason, WinSCP is throwing an error message. Thanks to Federico in the discussion for the correction.
- By default, the Microsoft SSH server does not run runs SFTP. I guess it can be enabled somehow, since the Windows 10 Mobile also includes SFTP server. There are definitely SFTP registry entries that the SSH broker tries to access. Some of them modify permissions, much like permissions for regular FTP.
Is it better than the OpenSSH for Windows?
I think not:
- it has obviously a very special purpose and it’s clearly not intended for an ordinary user
- the configuration options are very limited and most of them is inaccessible (you need to modify ownership and permissions on the registry keys). Obviously, you can have a list of possible login options, so you don’t have to allow password login.
On the other hand,
- the cmd.exe kinda doesn’t work correctly in the OpenSSH server (you’ll terribly miss arrows and Tab, for instance)
- one interesting thing, and I should maybe add -
!! A word of caution !!
OpenSSH for Windows will not respect the UAC! When you log in under an administrator account, you can even delete system files and the apps will run with the maximum rights that your user theoretically has!
Using OpenSSH for Windows, you can run non-interactive command-line apps and get output from them, and you can also try to run apps with UI. These will run, but without any window or anything shown on the screen! I found it interesting that even my account did not have access to the processes running under my account! And yet, these apps running under sshd had all the privileges any hacker could wish for. Let’s show a couple of shots:
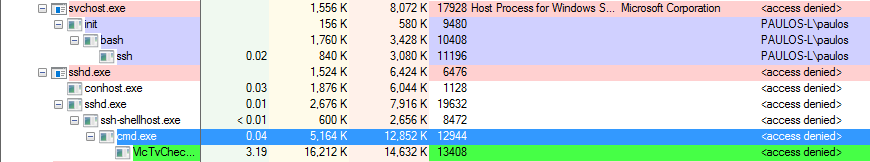

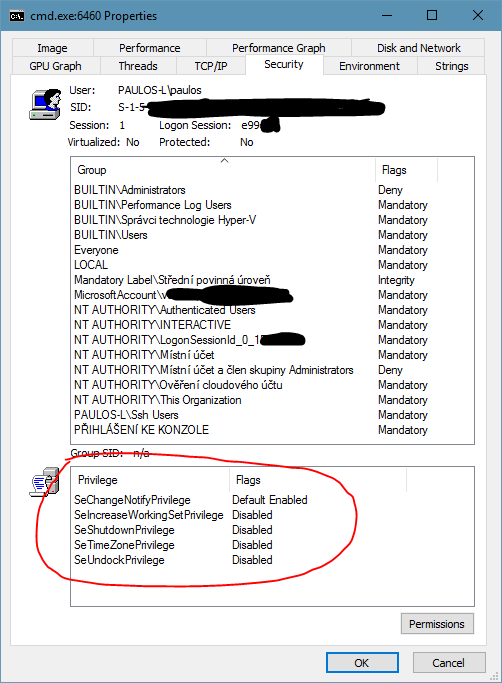
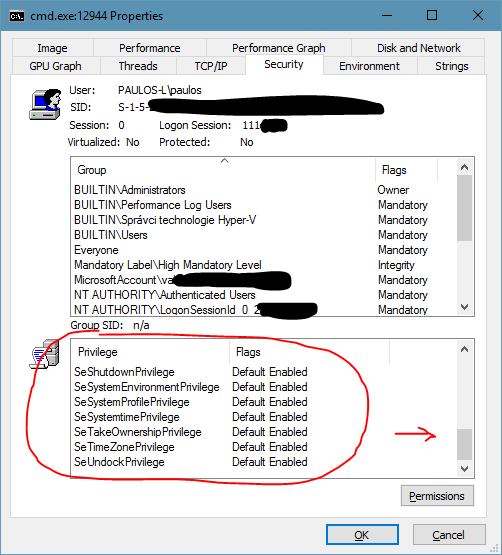
But, also, because this is OpenSSH, you have a lot more options to protect your account, for example with a keyfile, and disable password logon as an example. (So many articles have been written about the correct settings, but I’m not posting it since I haven’t tried it yet.) So, be careful, but definitely experiment, you’ll never know where it leads you!
Can I run Bash on OpenSSH for Win?
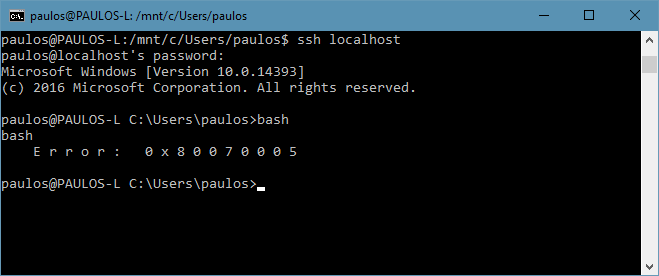
But… I have been able to run Bash under the DevToolsUser!
I can run more tests if there’s a demand, just write below!
Cheers!